Effective End-User Security Awareness Training
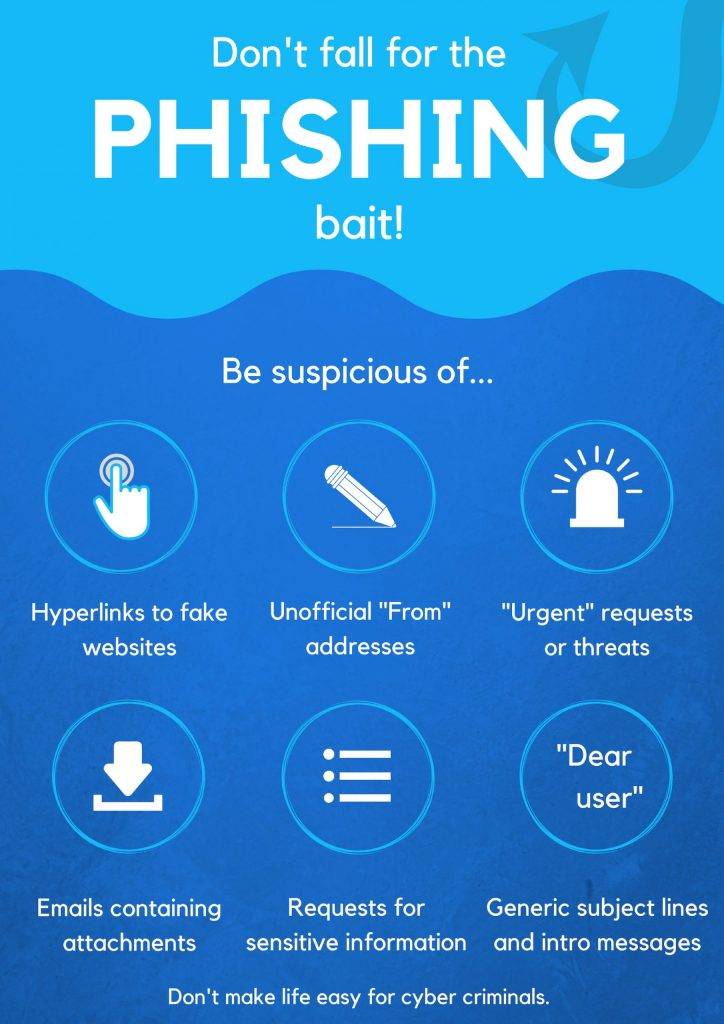
Security Awareness Training plays a major role in securing an organization as global statistics show that more than 90% of data breaches are caused by human errors. Mega breaches make the headlines on a daily basis, but there is also a growth in attacks on smaller companies. Many of them are vulnerable to attacks because of a lack of security awareness among employees. An effective security awareness training program can go a long way in helping organizations overcome this by educating the employees about the security best practices that need to be followed in an organization.
Employees are the weakest link in an organization when it comes to information security. Humans are born with an inner drive to explore the nature of their surroundings. We are often rewarded in our attempts to learn new things, solve puzzles, and win at games. But at the same time, the world around us teaches us rules of behavior that can restrict our inner urge towards free exploration.
Why? Because the human factor is truly security’s weakest link.
For scammers and hackers, following the inner urge offers great opportunity and thrills, letting them accomplish things that they believe cannot be done. Lack of security awareness leaves major gaps in cyber security that scammers or social engineers explore. Employees without proper security awareness can be deceived to give away sensitive information like passwords by scammers and hackers.
Why Employee Security Awareness Training?
Training employees to understand and avoid common security threats can significantly reduce an organization’s risk. Leveraging interactive training sessions, videos, tests, and optional phishing simulations, our security awareness training drives the behavioral change needed to shield your sensitive data every day.
Organizations need to be informed and prepared for what they’ll face during a cyber incident. Developing an awareness of cyber risks – what they are, ways to identify them, and the type of perpetrators – is one of the preferred approaches to combating the same from cyber threats. The danger of cybercrime remains a pervasive threat, with the majority of businesses reportedly falling victims to the attack. This is true for all employees of organizations irrespective of their role and seniority.
Cybercriminals target businesses mainly through employees (end-users). More than 80% of economic crime is committed by cybercriminals from information shared on social networks and other locations online to gain end users’ access and trust. When end users unknowingly click phishing links, open malware attachments, or give up credentials and other sensitive information online, cybercriminals can bypass existing layers of security to successfully breach organizations’ networks.
Security Awareness Training Topics
Our end-User Security Awareness training topics cover below training content followed by a test to evaluate the effectiveness of the training.
> Common Cybersecurity Myths
> Importance of Cyber Security in Business
> Security terms that you should know!!!
> Online habits that make you vulnerable to cyber attacks
> Information Security Practices – Physical Security & Workplace Security
> Online Safety – Internet & Email Security
> Removable media usage (USB & External Hard disks)
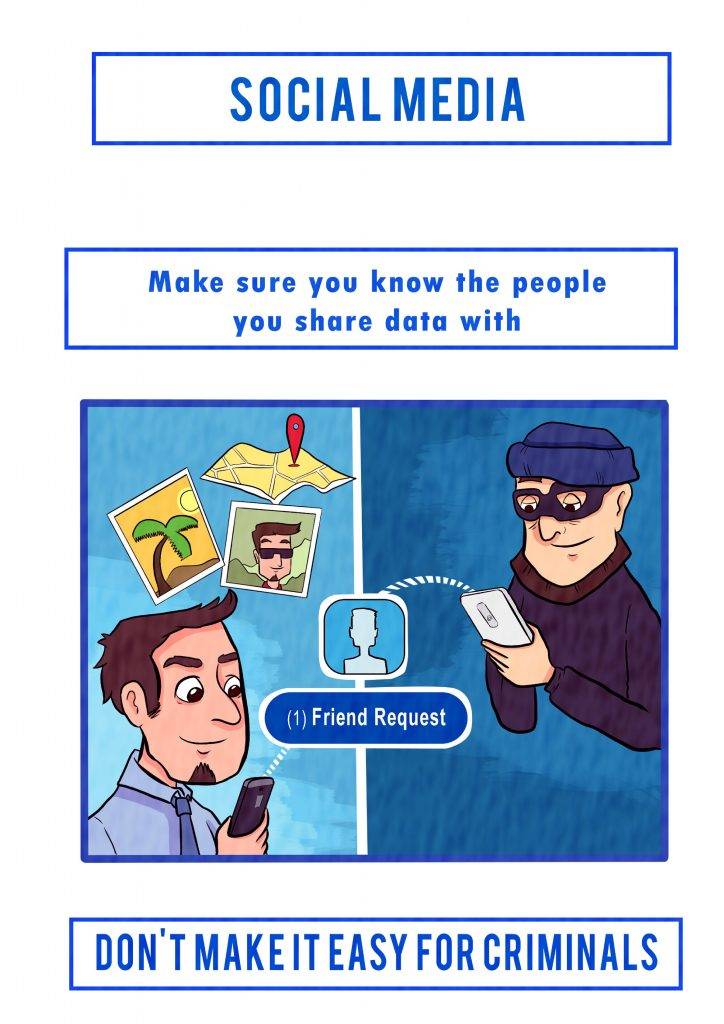
> Social Media usage
> Phishing attacks & Ransomware attacks
> Mobile & Voice Phishing
> Information Security Practices
> Email impersonation attacks and commonly ignored threats that hackers exploit
> Shoulder Surfing & Tailgating
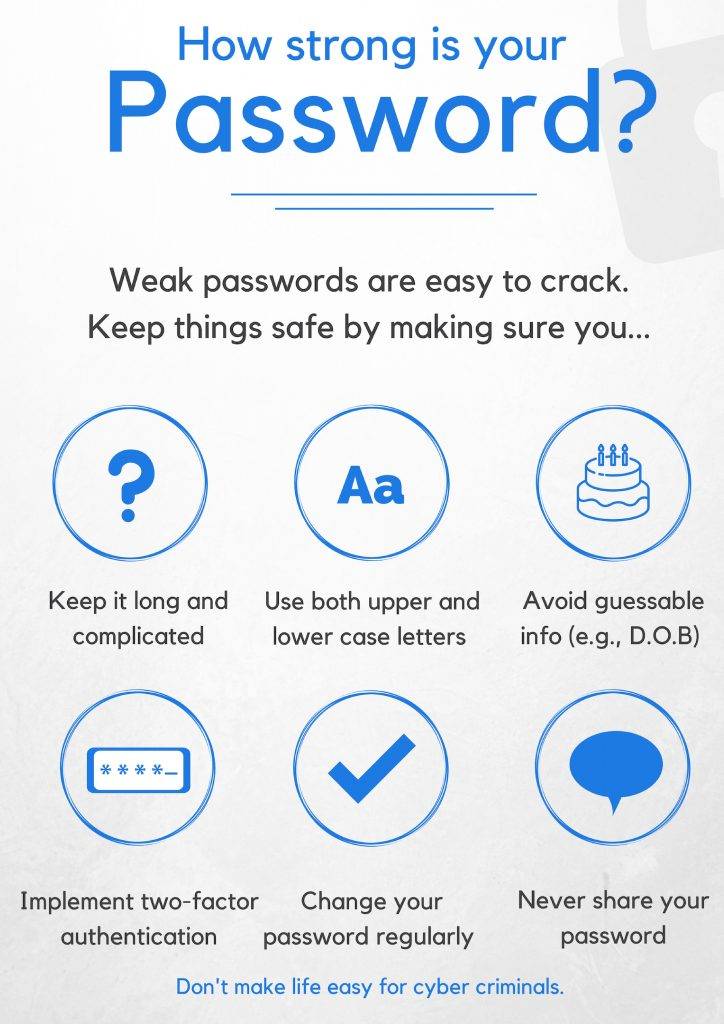
> Password Management & Most hacked passwords
> Protecting your data while using Wi-Fi
> Why cybersecurity is important for Senior Management
> Commonly used Attack scenarios
> Recent cybersecurity news that made the headlines
> How to distinguish between genuine and fake messages
> Attacks that you should be aware of – Fileless Malware, Banking Malware, Rouge browser extensions, Holiday/festival scams, Sextortion, Starkerware, Mobile Security Threats, WhatsApp attacks, ATM Skimming. Phishing, IoT Attacks, Voice attacks, Pandemic/Corona themed attacks, Domain fraud, Bitcoin scams, Remote Access Trojans, Risk with the usage of public USB Chargers & USB devices, AI-powered attacks, Deep fake attacks, Executive Impersonation
Creative security awareness training helps employees effectively overcome their IT security weaknesses while using the internet, and social media platforms for personal and official purposes. We deliver Security awareness training sessions in English & Arabic in the form of Presentations with Videos, Games, Animations, Posters, Infographics, etc. We have qualified cybersecurity trainers with certifications like ISO/IEC 27001, CISA, CISSP, HISP, etc. who have conducted multiple security awareness training sessions in UAE & Middle East.
End-User Security awareness training topics that we cover include the importance of cybersecurity for business, essential cybersecurity habits, password management, email impersonation attacks, Pandemic/Corona-themed attacks, Banking Malware, Holiday/festival scams, Sextortion, Starkerware, Mobile Security Threats, WhatsApp attacks, and ATM Skimming.
Other cybersecurity topics that we cover are Ransomware attacks, Fileless Malware, Phishing, IoT Attacks, Voice attacks, Zero Trust Security, Domain fraud, Bitcoin scams, Remote Access Trojans, AI-powered attacks, Deep fake attacks, Privileged User Misuse, Rogue browser extensions, and Executive Impersonation. Getting your employees trained with effective security awareness training equips them with proper cybersecurity knowledge and the right cybersecurity skills to reduce the cyberattacks targeted at businesses.
Only a holistic security strategy paired with a deep understanding of the business processes can minimize the security risk of an organization. Technical security measures must always be combined with organizational measures. The successful sensitization of the employee begins with the awakening of interest in the subject. The user then wants to know why different information security measures are introduced and will then gain an understanding of this. Because she/he now understands and accepts, they will act accordingly.
Get Free Security Awareness Posters now !!
Social Engineering Simulation
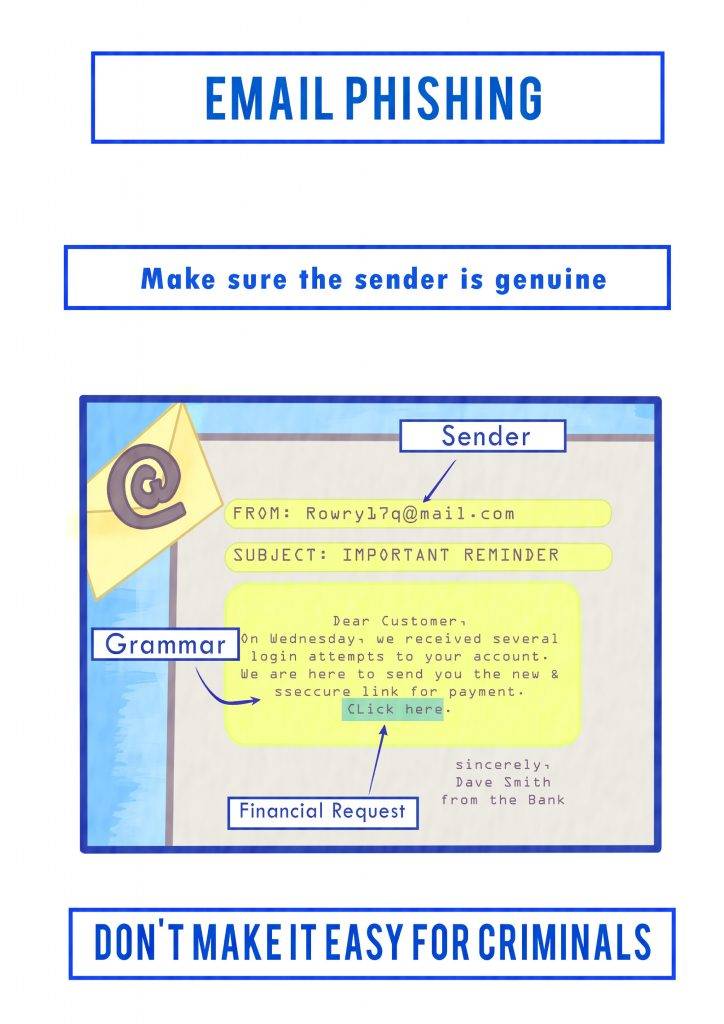
Social engineering is the process of tricking users to give away passwords and other credentials using various techniques. Social Engineering simulation tools can launch dummy cyber attacks on employees to evaluate how they react to such attacks. We can simulate the top attack vectors used by hackers – Phishing and Smishing.
Phishing or fraudulent email is the most prevalent and successful tactic used in advanced targeted attacks. In fact, ninety-one percent of targeted attacks use spear phishing. In recent years, a clear majority of data breaches have begun with spear phishing. We use a similar technique to compromise a target host to check the effectiveness of existing security systems. This could be used in real life by attackers to either launch a whaling attack against senior executives or spear phishing for privileged users which can lead to an APT attack. Smishing involves sending fake SMS messages to target users.
We would be conducting a test against customer employees to identify if they are susceptible to such attacks and if the perimeter security is strong enough to protect against such exploitation attempts.
Our team executes a phishing assessment with the following steps:
1. Reconnaissance and Information Gathering – The collection of information is a critical stage of social engineering and often determines the success of the rest of the phishing assessment. Using a ‘black box’ approach, our security experts perform in-depth research to extract information on the target company.
2. Create Pretext Scenarios and Payloads – Once we have fully enumerated the target, the focus turns to craft the payload. These specifics include identifying departments, user roles, and associated pretext scenarios. These details ensure each user is researched thoroughly for the most successful, targeted engagements.
3. Engage Targets – Using carefully structured tactics and pretexts, our security analysts engage employees via phishing emails. These emails often prompt users to interact by clicking a link or downloading a malicious file. The emails and subsequent landing pages are crafted to appear authentic, often mimicking other sites and services.
4. Assessment Reporting and Debrief – After completing the campaign and aggregating results, a final report is delivered, providing both an executive summary and specific details. The report also includes a thorough breakdown of risk, as well as remediation steps and documentation of successful phishing attempts. Training guides are also offered, guiding the client in resolving the training and policy issues identified.
5. Optional Security Awareness Training – As an optional addition, our team provides user training sessions for client employees. Whether hosted in a recorded online webinar or an in-house training session, we provide quality security awareness training by the same experts who performed the original engagement.
Benefits of Social Engineering Simulation
Lesser Cybersecurity Incidents:- Security awareness training helps to reduce the likelihood of the success of phishing and other cybercrime attacks by educating staff on current tactics and defense mechanisms.
Reduce Attack Vectors:- With over 90% of successful attacks attributed to user error, educating users through computer-based training is proven to reduce these odds significantly.
Better Security:-New tactics and techniques are constantly being adopted by cybercriminals. Ongoing user training ensures you are kept up to date on the latest methods of attack, so they stay on track and out of trouble.
Regulatory Compliance:- Internet security awareness training is not only best practice in many industries, but it’s also a requirement for a number of industry sectors to ensure compliance with regulations like ISO 27001, HIPAA, PCI DSS, etc.
Continuous Security Awareness Training
We also provide ongoing cyber awareness training using an online training platform called usecure, which can be launched in minutes. It uses a short gap analysis questionnaire to identify each user’s weakest areas of security, gathering results into their unique risk profile to baseline end-user security awareness training. Using your employees’ risk profiles the security awareness platform will auto-enroll users onto personalized training programs that tackle their unique risks — with course topics being prioritized based on their weakest areas. It helps you to understand how your users are progressing with company-wide risk scoring individual user performance and automate summary reports for managers.
It helps to measure, boost, and monitor your employee’s cybersecurity awareness. You can identify your staff’s individual security blind spots and automate the fix with user-tailored training programs.
Deploy with ease:- 100% cloud-based, installation-free and simple configuration.
Automate training:- Save time by automating repetitive admin tasks.
Build risk profiles:- Understand your users’ biggest security vulnerabilities.
Target risk areas:- Prioritize courses that eliminate users’ unique risk areas.
Track progress:- View real-time performance and enable weekly summaries.
Video & Interactive:- Help users retain information with a short video and interactive learning.
Micro-Learning:- Keep users engaged with bite-sized, jargon-free courses.
Simulated Phishing:- Launch attack simulations and instantly educate at-risk users about phishing emails so that they can report phishing.
User-personalized:- Deliver programs that target each user’s unique risks.
Custom LMS:- Build custom courses with an intuitive drag-and-drop LMS.
Compliance Courses:- Enrol users with readily-made compliance courses.
Fun & Corporate:- Choose between corporate-friendly and fun training solution styles.
Amazing Support:- Get helpful support via live chat, or visit our Help Centre.