SOC in a Box
SOC in a Box is a managed security offering with integrated NDR, SIEM, Intrusion Detection, Network Traffic Analysis, SOAR, Automated Threat Hunting, and Forensics. It involves automated detection of threats using a single platform to detect & Respond with 24×7 analysis and support by Security experts. Logs and other data collected by the appliance can stay within the premise or the on-cloud.
SOC in a Box is a 24/7 Managed Security Service offering that comes with security monitoring and incident response with a starting price of AED 5,000 per month.
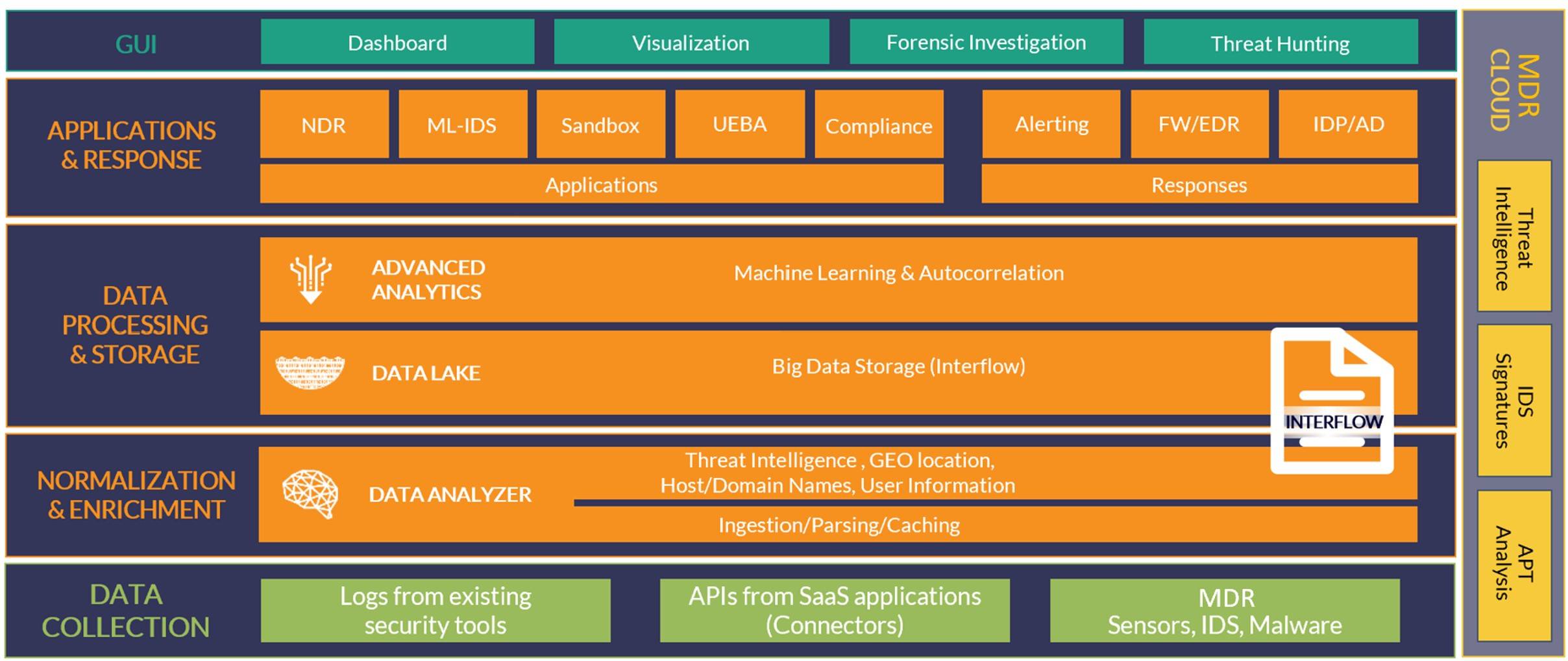
CrossCipher SOC in a Box offering is powered by a revolutionary technology, which is a unified, AI-powered approach to detection and response, that collects and correlates all existing security tools, to protect the entire attack surface effectively and efficiently. It is more than SIEM because it must defend against all threats across the entire attack surface. The only way to do this is by integrating with all existing security tools. AI and automation come in as the only technically feasible way of protecting the entire attack surface effectively and efficiently, which is why it is a key architectural attributes of our services.
We typically deploy a virtual appliance at the customer’s premises to initiate the engagement. The appliance will collect logs from critical devices and collect live traffic data by configuring the span port on the core switch. Throughout the period of operation, key deliverables provided to the customer include:
- > Intrusion Detection
- > Integration with existing EDR solutions
- > SIEM & Log Management
- > Behavioral Monitoring
- > Ransomware Detection & Response
- > Security & Compliance Reporting
- > Network Monitoring
CrossCipher platform is a unified platform for Security Operations, providing a central location to gather and organize security threat information by unifying key data, tools, and alerts for analysis. Our platform also automates both threat detection (using AI and machine learning) and response (using automated threat hunting). This helps reduce the noise so you aren’t overwhelmed by the amount of information and can find and focus on the real threats. Our security analysts can even teach machine learning to present only the information that truly interests you.
Our experience has shown that clients have benefitted greatly from partnering with us both in terms of financial/business security and intellectual property safety.
SOC in a Box offering
As a Managed Security Service, we deliver a proactive managed cybersecurity solution. This is much more than Software as a Service and goes well beyond mere “alerting”. SOC in a Box brings together Security Information and Event Management (SIEM), Network Security Monitoring, Endpoint Monitoring, Audit Assistance, and Business Intelligence, making them operate as a single system. Further, in a time when the threat landscape evolves and becomes sophisticated, it is not enough for your Cybersecurity team to be “just functional,” it needs to be constantly aware and intelligent.
SOC in a Box Features
Main Features
SOC in a Box achieves optimal results not by developing another security product, but by integrating the industry-best security solutions through the integration playbook. This makes it a unique service offering that will custom work for the client and not force upon a canned vendor-dependent expensive solution by providing the most appropriate and cost-effective custom Security Monitoring solution in the market.
Next-gen SIEM
The SIEM platform provides a real-time correlation of events generated from network security controls and logs. Our security gurus will explain what SIEM is (and isn’t) and how to get up and running with it quickly and painlessly.
Threat Intelligence
Our platform is integrated with Threat Intelligence Platform (TIP), which is a cloud-based platform that automatically collects and aggregates feeds from many different sources into a single consolidated resource of threat intelligence. TIP sources include commercial and open-source threat intelligence from organizations such as Proofpoint, DHS, OTX, Openphish, and PhishBank, from internal research, or shared by other deployments.
Network Traffic Analysis
Network Monitoring is a component of the SOC in a Box solution that provides web-based network traffic analysis and network flow collection. It sorts network traffic according to many criteria including IP address, port, protocols, and Autonomous Systems (AS) to show real-time network traffic and active hosts. It produces long-term reports for several network metrics including throughput and application protocols and monitors and reports live throughput, network and application latencies, Round Trip Time (RTT), TCP statistics (retransmissions, out-of-order packets, packet lost), and bytes and packets transmitted.
Forensics
A complete and comprehensive approach to forensics is essential to any investigation. Using the most advanced cloning techniques to recover all forms of digital evidence, we accurately recreate past events so that you can take the appropriate action.