- July 8, 2017
- Posted by: admin
- Categories: IT Security, Ramsomware
Heimdal CORP users can enjoy the benefits of machine learning insights that fuel even stronger protection against advanced and sophisticated malware.
Heimdal announces the launch of a landmark enhancement to DarkLayer GUARD engine, called VectorN Detection. This is the result of coordinated, hard work between the Heimdal team and strategic partners that share the same values and dedication for online security.
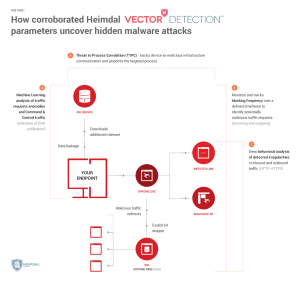
VectorN Detection will focus on ensuring Code Autonomous ProtectionTM on both endpoints, detecting malware in ways that no other endpoint protection can.
A few key things you should know about VectorN Detection :
- It works across-the-board on any Windows™ device;
- It does not rely on scanning the code or auditing any system processes. Instead, the new technology uses Machine Learning Detection (MLD) to perform an in-depth analysis of all incoming and outgoing HTTP, HTTPS and DNS traffic.
- It matches Machine Learning (MLD) insights with Indicators of compromise/attack (IOC/IOA) and network forensics, turning Heimdal CORP and Heimdal PRO into unique, proactive cybersecurity suites.
- It helps users discover even hidden, second-generation malware that tries to infect the endpoint or attempts to harvest data from the compromised system.
- By tracking device-to-infrastructure communication, this technology enables users to detect and block advanced malware, regardless of the attack vector.
Heimdal CORP works proactively to detect APTs, ransomware strains, botnets. Trojans and more, while blocking them until removed from the system.
HeimdalTM enables users to close vulnerabilities and mitigate exploits, while constantly blocking incoming attacks, data leakage and Command & Control server communication.
What you need to know about Darklayer GUARDTM
HeimdalTM has a unique, client-based two-way Traffic Scanning Engine that detects and blocks network communication to mitigate Zero Hour exploits, ransomware C&Cs, malware backbones, next-generation attacks, and data leakage.
In addition to blocking the source of threat by analyzing traffic-based communication, the Threat to Process Correlation (TTPC) technology will also identify the malicious process, enabling endpoint owners to act fast in containing and cleaning the potential infection. When malware tries to compromise your computer, you’ll know which application or process it’s trying to infect, so you can stop attackers in their tracks.